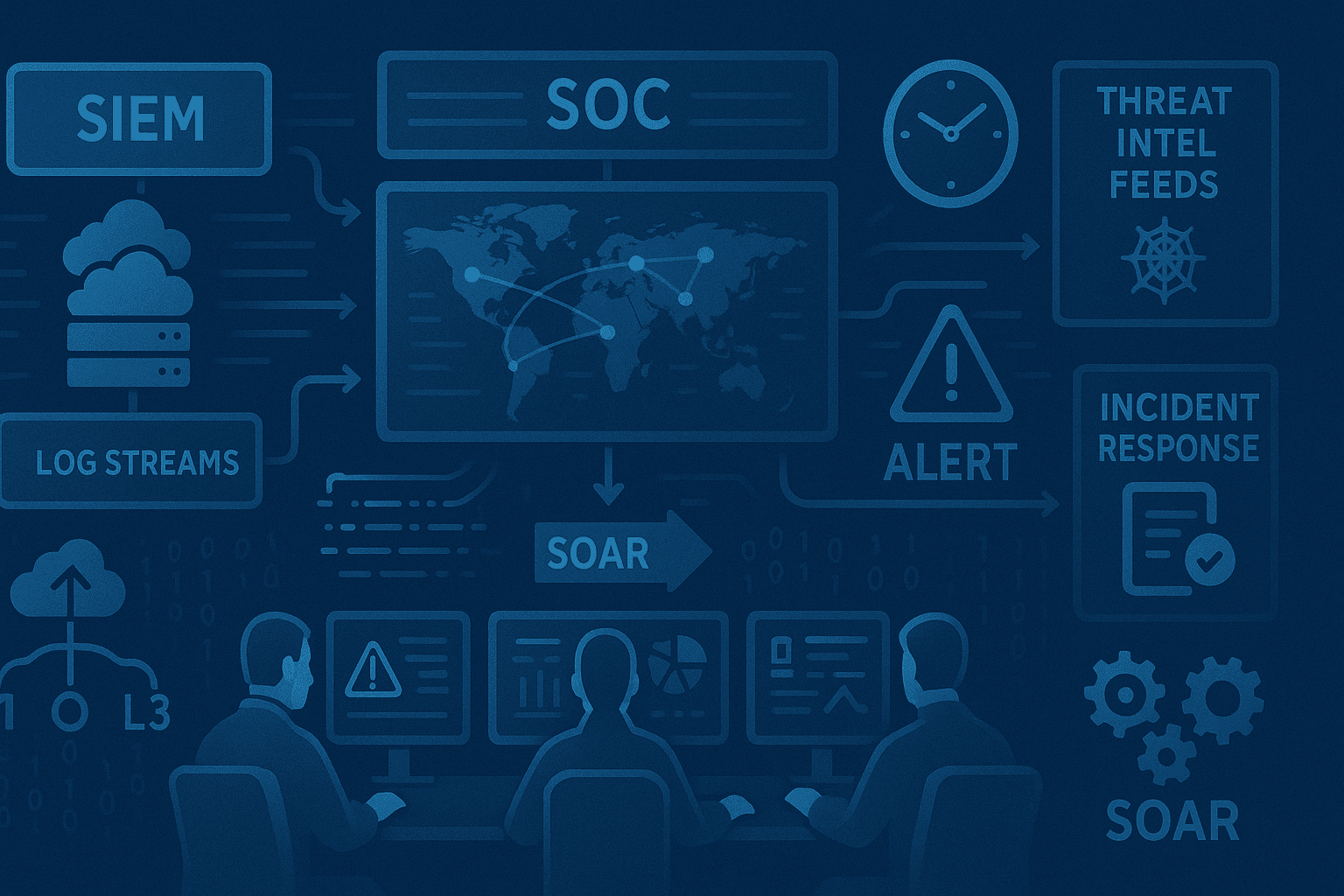
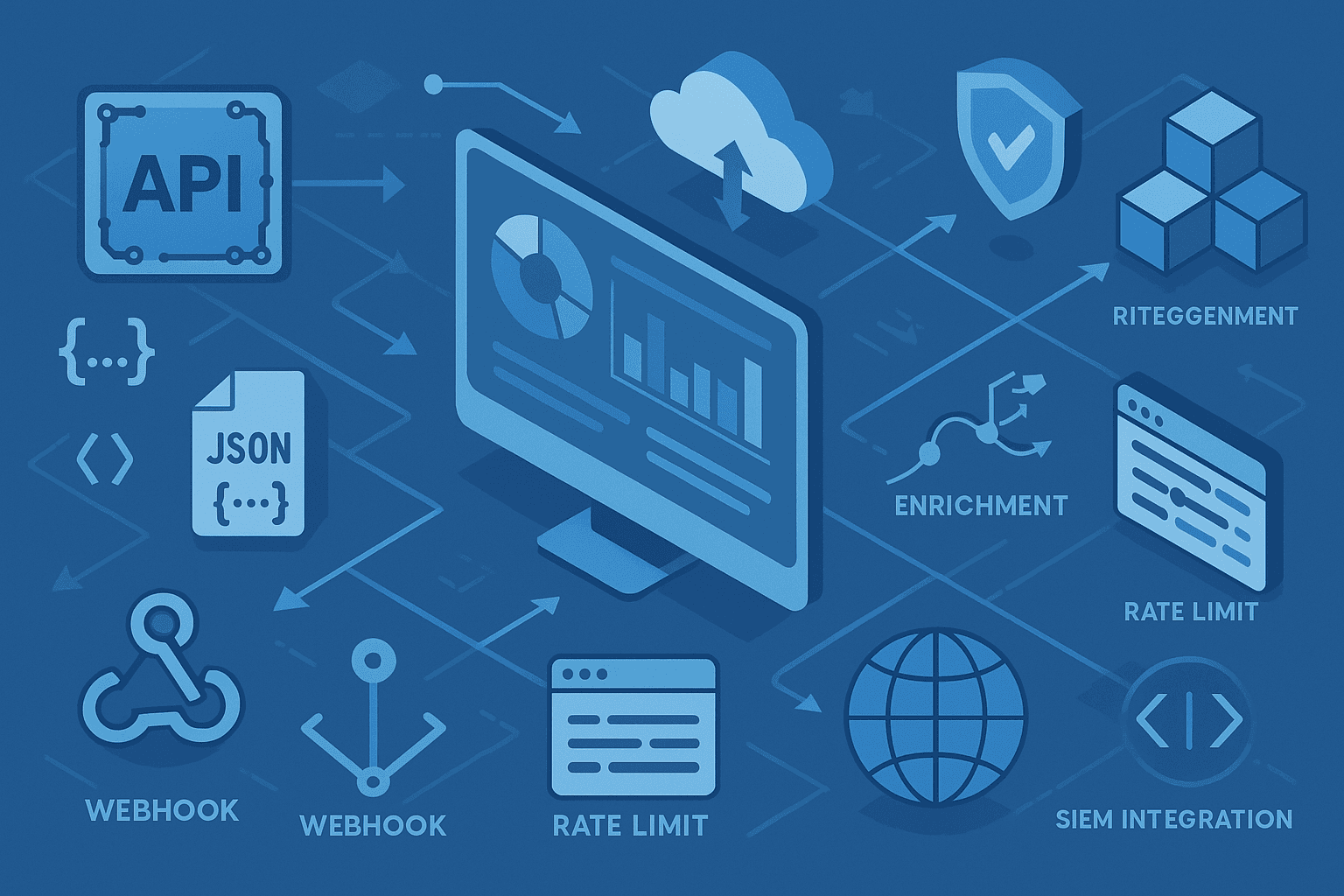
SOC Teams
Threat intelligence for security operations
Empower your analysts with real-time threat intelligence. Reduce alert fatigue, accelerate investigations, and improve detection accuracy.
Key Features
Everything you need to protect your infrastructure and users
Real-Time Enrichment
Instantly enrich alerts with threat context and risk scores.
Alert Prioritization
Focus on high-risk alerts with confidence-based scoring.
Investigation Tools
Pivot on IOCs with related threats and historical data.
Live Dashboards
Monitor threat landscape with real-time visualizations.
Custom Alerting
Get notified when specific threats or patterns emerge.
Team Collaboration
Share findings and coordinate response across the team.
Use Cases
How security teams use this tool
Alert Triage
Quickly assess alert severity with threat context.
Threat Hunting
Proactively search for IOCs across your environment.
Incident Investigation
Deep-dive into threats with enrichment data.
Reporting
Generate executive reports on threat landscape.
Transforming SOC Efficiency with Threat Intelligence
Security Operations Centers are drowning in alerts. Analysts spend countless hours investigating low-confidence detections while real threats slip through. The missing ingredient? Context. Threat intelligence provides the context needed to separate signal from noise. When an alert fires, knowing whether the associated IP has a history of malicious activity, or if the domain was registered yesterday and is hosting known malware - that context transforms investigation from guesswork to precision.
Reducing Alert Fatigue and False Positives
Alert fatigue is the enemy of effective security operations. Our threat intelligence helps reduce false positives in several ways: - **Risk Scoring**: Every IP, domain, and URL receives a confidence-weighted risk score based on multiple intelligence sources - **Context Enrichment**: Analysts see registrar data, hosting info, SSL certificate details, and historical behavior at a glance - **Category Classification**: Know immediately if an entity is associated with malware, phishing, spam, or other threat types - **Age Analysis**: New domains and recently-changed registrations are flagged for extra scrutiny With this context, analysts can confidently dismiss low-risk alerts and focus on genuine threats.
Accelerating Incident Investigation
When a potential incident is identified, speed matters. Our platform accelerates investigations: - **Pivot on IOCs**: From any indicator, explore related domains, IPs, and infrastructure - **Historical Data**: See how an entity's reputation has changed over time - **Related Threats**: Identify if an IOC is connected to known campaigns or threat actors - **API Integration**: Pull enrichment data directly into your case management tools - **Bulk Analysis**: Quickly assess hundreds of IOCs from a compromise Turn hours of manual research into seconds of automated enrichment.
Proactive Threat Hunting with Intelligence
Modern SOCs don't just respond to alerts - they actively hunt for threats. Our intelligence enables effective hunting: - **Fresh IOC Feeds**: Hunt for indicators from the latest threat campaigns in your environment - **Trend Analysis**: Identify emerging threats and threat actor TTPs - **Custom Alerting**: Set up alerts when specific threat categories or actors target your industry - **Integration with Hunting Tools**: Works with Jupyter notebooks, SIEM queries, and custom scripts Move from reactive to proactive security operations.
Frequently Asked Questions
How does threat intel reduce alert fatigue?
What integrations are available?
How fresh is the threat data?
Can we customize the feeds?
Related Articles
Learn more from our security research blog
Ready to Get Started?
Join thousands of security teams using isMalicious to protect their infrastructure.