Building a Modern SOC with Threat Intelligence: A Practical Guide
 Jean-Vincent QUILICHINI
Jean-Vincent QUILICHINI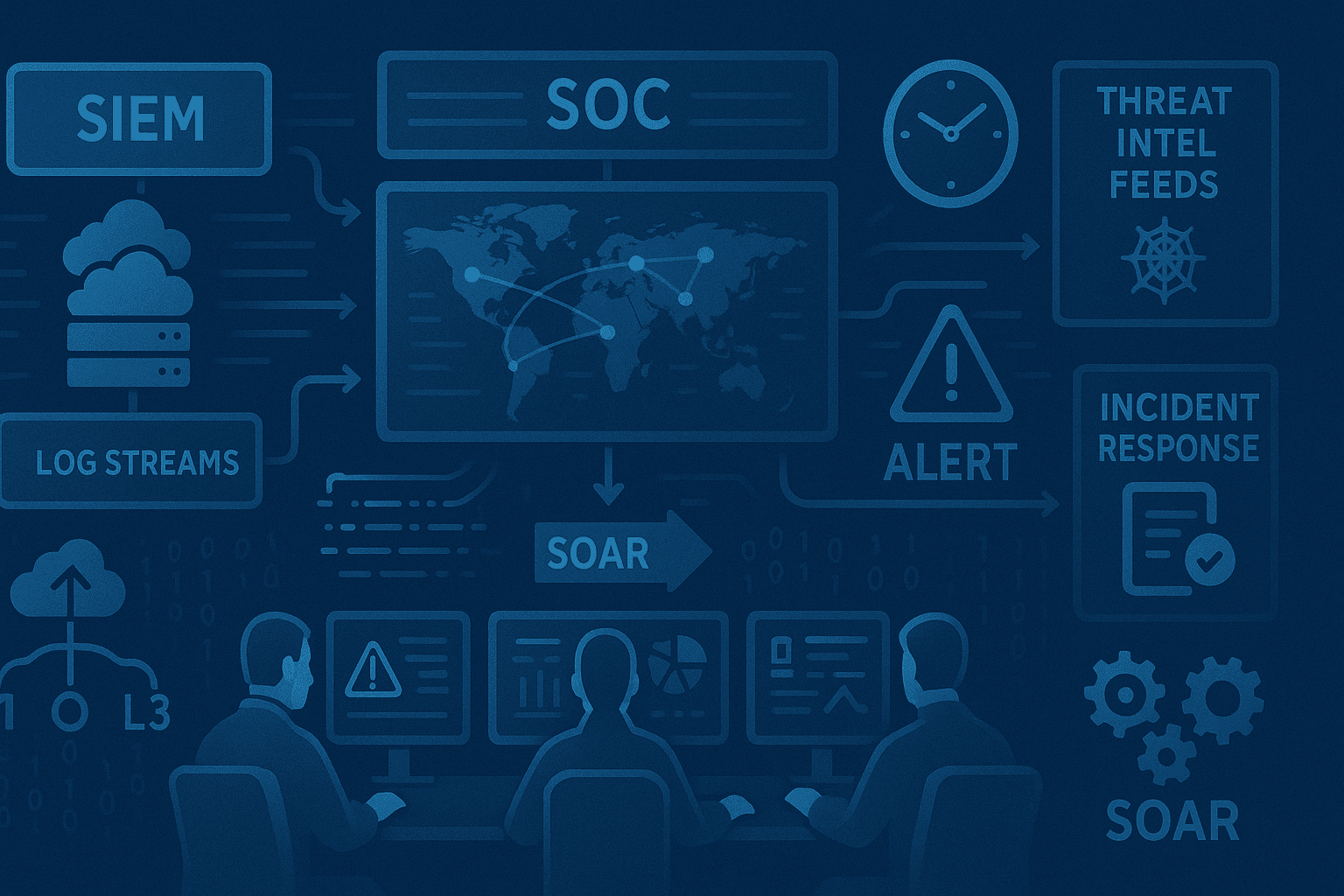
A Security Operations Center (SOC) serves as the nerve center of an organization's cybersecurity defense. By combining skilled analysts, advanced technology, and comprehensive threat intelligence, a well-designed SOC can detect and respond to threats before they cause significant damage. This guide explores how to build a modern, intelligence-driven SOC that effectively protects your organization.
Understanding the Modern SOC
A SOC is a centralized unit that monitors, detects, analyzes, and responds to cybersecurity incidents. Unlike traditional reactive approaches, modern SOCs leverage threat intelligence to proactively identify and mitigate risks.
Core SOC Functions
- Continuous Monitoring: 24/7 surveillance of networks, systems, and applications.
- Threat Detection: Identifying anomalies and potential security incidents.
- Incident Response: Containing and remediating security breaches.
- Threat Intelligence: Gathering and analyzing information about cyber threats.
- Forensics and Investigation: Understanding attack methods and attribution.
- Compliance Management: Ensuring adherence to regulatory requirements.
SOC Maturity Levels
Level 1: Reactive SOC
Responds to alerts and incidents after they occur. Limited threat intelligence integration and primarily dependent on automated tools.
Level 2: Proactive SOC
Actively hunts for threats and uses basic threat intelligence feeds. Implements some preventive controls based on known indicators.
Level 3: Intelligence-Driven SOC
Fully integrated threat intelligence informs all security decisions. Predictive analytics and advanced threat hunting are standard practices.
Level 4: Adaptive SOC
Uses machine learning and AI for autonomous threat detection and response. Continuously evolves based on the threat landscape.
Essential SOC Team Roles
SOC Analyst (Tier 1)
First line of defense, monitoring alerts and performing initial triage:
- Monitor SIEM dashboards and security alerts.
- Classify and prioritize security events.
- Escalate suspicious activity to Tier 2.
- Document incidents and maintain logs.
Incident Responder (Tier 2)
Deep-dive analysis and incident handling:
- Investigate escalated security incidents.
- Perform threat hunting activities.
- Coordinate incident response efforts.
- Develop containment strategies.
Threat Hunter / Senior Analyst (Tier 3)
Advanced threat detection and intelligence analysis:
- Proactive threat hunting using advanced techniques.
- Develop threat intelligence from various sources.
- Reverse-engineer malware and attack techniques.
- Create custom detection rules and signatures.
SOC Manager
Oversees operations and strategic direction:
- Manage SOC team and resources.
- Define metrics and performance indicators.
- Coordinate with other business units.
- Report to executive leadership on security posture.
Core SOC Technologies
1. Security Information and Event Management (SIEM)
Centralized log collection and correlation platform:
- Aggregates logs from all security tools and infrastructure.
- Correlates events to detect complex attack patterns.
- Provides dashboards and real-time alerts.
Popular Solutions: Splunk, IBM QRadar, Microsoft Sentinel, Elastic Security
2. Endpoint Detection and Response (EDR)
Monitors endpoint activities for malicious behavior:
- Detects advanced threats on workstations and servers.
- Provides forensic data for investigation.
- Enables remote containment and remediation.
Popular Solutions: CrowdStrike Falcon, Microsoft Defender for Endpoint, SentinelOne
3. Network Detection and Response (NDR)
Analyzes network traffic for threats:
- Identifies lateral movement and data exfiltration.
- Detects encrypted threat communication.
- Provides network visibility and forensics.
Popular Solutions: Darktrace, ExtraHop, Vectra AI
4. Threat Intelligence Platform (TIP)
Aggregates and manages threat intelligence:
- Collects data from multiple intelligence sources.
- Enriches security events with context.
- Automates indicator sharing and blocking.
Popular Solutions: Anomali, ThreatConnect, MISP
5. Security Orchestration, Automation, and Response (SOAR)
Automates response workflows:
- Standardizes incident response processes.
- Automates repetitive security tasks.
- Integrates multiple security tools.
Popular Solutions: Palo Alto Cortex XSOAR, Splunk SOAR, IBM Resilient
Integrating Threat Intelligence
Threat intelligence transforms a SOC from reactive to proactive. Effective integration requires:
Strategic Intelligence
Understanding adversary motivations, capabilities, and trends:
- Industry-specific threat landscape analysis.
- Geopolitical factors affecting cyber risk.
- Emerging attack techniques and tools.
Tactical Intelligence
Information about adversary tactics, techniques, and procedures (TTPs):
- Attack patterns and methodologies.
- Tools and malware used by threat actors.
- Infrastructure and command-and-control patterns.
Operational Intelligence
Real-time information about active campaigns and threats:
- Ongoing attack campaigns targeting your industry.
- Indicators of compromise (IoCs) from recent incidents.
- Vulnerability intelligence and patch priorities.
Technical Intelligence
Specific indicators for detection and blocking:
- Malicious IP addresses and domains.
- File hashes of known malware.
- URL patterns used in phishing campaigns.
- Network signatures for threat detection.
How isMalicious Enhances Your SOC
isMalicious provides essential threat intelligence for modern SOCs:
Real-Time Threat Feeds
- 500M+ Threat Indicators: Comprehensive database of malicious IPs, domains, and URLs.
- Continuous Updates: Daily refreshes ensure protection against latest threats.
- Multi-Category Intelligence: Malware, phishing, C2, spam, and more.
Automated Integration
- RESTful API: Easy integration with SIEM, SOAR, and other security tools.
- Customizable Queries: Filter intelligence based on your specific needs.
- High Performance: Sub-second response times for real-time blocking.
Enrichment and Context
- Comprehensive Threat Profiles: WHOIS, geolocation, ASN, and historical data.
- Risk Scoring: Prioritize investigations based on threat severity.
- Similarity Analysis: Discover related threats and campaigns.
Proactive Monitoring
- Asset Watching: Monitor your IPs and domains for emerging threats.
- Alert Notifications: Instant alerts when watched assets become suspicious.
- Trend Analysis: Understand threat patterns affecting your infrastructure.
Building SOC Processes
1. Alert Triage Process
Standardize how alerts are handled:
- Classification: Categorize alerts by type and severity.
- Prioritization: Focus on high-impact, high-likelihood threats first.
- Initial Assessment: Gather basic facts before escalation.
- Documentation: Record all findings and actions taken.
2. Incident Response Playbooks
Create documented procedures for common scenarios:
- Malware infections.
- Phishing campaigns.
- Data exfiltration attempts.
- DDoS attacks.
- Insider threats.
- Ransomware incidents.
3. Threat Hunting Framework
Develop hypothesis-driven investigations:
- Hypothesis Formation: Based on threat intelligence and industry trends.
- Data Collection: Gather relevant logs and telemetry.
- Analysis: Look for evidence supporting or refuting the hypothesis.
- Documentation: Record findings and create new detection rules.
4. Continuous Improvement
Regularly assess and enhance SOC effectiveness:
- Metrics Review: Analyze KPIs like MTTD (Mean Time to Detect) and MTTR (Mean Time to Respond).
- Post-Incident Reviews: Learn from each incident.
- Red Team Exercises: Test defenses with simulated attacks.
- Training: Keep analysts updated on latest threats and techniques.
SOC Metrics and KPIs
Measure SOC performance with these key indicators:
Detection Metrics
- Mean Time to Detect (MTTD): Average time to identify security incidents.
- True Positive Rate: Percentage of alerts that are genuine threats.
- False Positive Rate: Percentage of alerts that are false alarms.
- Coverage: Percentage of infrastructure with monitoring.
Response Metrics
- Mean Time to Respond (MTTR): Average time to contain and remediate incidents.
- Mean Time to Recovery (MTTR): Time to restore normal operations.
- Escalation Rate: Percentage of incidents requiring escalation.
Intelligence Metrics
- Threat Intelligence Usage: Percentage of investigations enriched with intelligence.
- IoC Hit Rate: How often intelligence indicators match real threats.
- Intelligence Freshness: Age of threat data being used.
Operational Metrics
- Analyst Productivity: Incidents handled per analyst.
- Automation Rate: Percentage of tasks automated.
- Training Hours: Time invested in analyst development.
Common SOC Challenges and Solutions
Challenge: Alert Fatigue
Problem: Analysts overwhelmed by high volumes of alerts, leading to burnout and missed threats.
Solutions:
- Tune SIEM rules to reduce false positives.
- Implement automation for routine tasks.
- Use risk-based prioritization.
- Leverage threat intelligence for better context.
Challenge: Skills Gap
Problem: Difficulty finding and retaining skilled security analysts.
Solutions:
- Invest in training and certification programs.
- Develop career progression paths.
- Use automation to augment junior analysts.
- Partner with MSSPs for specialized expertise.
Challenge: Tool Sprawl
Problem: Too many disconnected security tools create complexity.
Solutions:
- Consolidate vendors where possible.
- Implement SOAR for integration.
- Standardize on key platforms.
- Regularly review tool effectiveness and usage.
Challenge: Threat Intelligence Overload
Problem: Too much threat data without proper context or actionability.
Solutions:
- Focus on high-quality, relevant sources.
- Implement automated correlation and enrichment.
- Use threat intelligence platforms for management.
- Prioritize tactical and operational intelligence.
Cloud-Native SOC Considerations
Modern SOCs must adapt to cloud environments:
Cloud Security Monitoring
- Monitor IaaS, PaaS, and SaaS environments.
- Integrate cloud provider security tools (AWS Security Hub, Azure Security Center, GCP Security Command Center).
- Implement Cloud Security Posture Management (CSPM).
Container Security
- Monitor container runtime security.
- Scan images for vulnerabilities.
- Implement Kubernetes security policies.
Multi-Cloud Complexity
- Maintain visibility across multiple cloud providers.
- Standardize security controls where possible.
- Use cloud-agnostic security platforms.
Compliance and Regulatory Alignment
Ensure your SOC meets industry requirements:
- PCI DSS: Requires continuous monitoring and incident response capabilities.
- HIPAA: Mandates security incident procedures and breach notification.
- GDPR: Requires ability to detect and report breaches within 72 hours.
- SOC 2: Demands documented monitoring and incident response processes.
- ISO 27001: Includes requirements for security operations and monitoring.
SOC as a Service (SOCaaS)
For organizations without resources to build an in-house SOC:
Benefits
- Access to experienced analysts 24/7.
- Lower initial investment compared to building SOC.
- Flexibility to scale based on needs.
- Access to advanced tools and threat intelligence.
Considerations
- Less control over operations and priorities.
- Potential communication challenges.
- Data privacy and compliance concerns.
- Need for clear SLAs and performance metrics.
The Path Forward
Building an effective SOC is an ongoing journey, not a destination. Start with:
- Assess Current State: Understand your existing capabilities and gaps.
- Define Requirements: Based on your risk profile and business needs.
- Build Incrementally: Start with core capabilities and expand over time.
- Integrate Intelligence: Make threat intelligence central to operations.
- Measure and Improve: Continuously refine based on metrics and lessons learned.
Strengthen Your SOC Today
A well-designed SOC powered by quality threat intelligence is your best defense against modern cyber threats. By combining the right people, processes, and technology, you can detect and respond to threats faster and more effectively.
Ready to enhance your SOC with comprehensive threat intelligence? Explore isMalicious and give your security team the intelligence they need to stay ahead of evolving threats. Start building a more resilient security operation today.
Protect Your Infrastructure
Check any IP or domain against our threat intelligence database with 500M+ records.
Try the IP / Domain Checker