Harnessing Public Sources for IP and Domain Maliciousness Detection
 Jean-Vincent QUILICHINI
Jean-Vincent QUILICHINI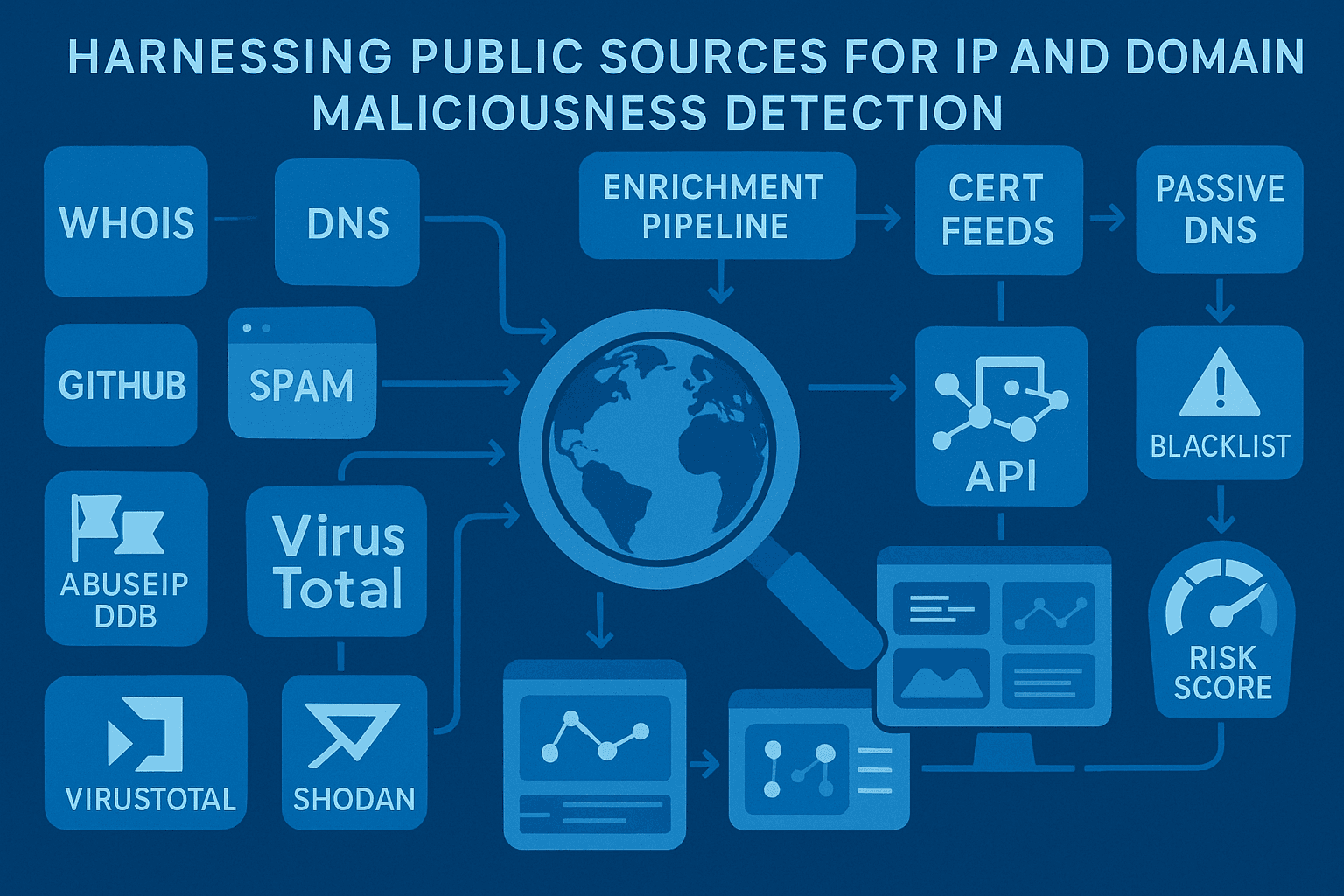
The internet is rife with malicious actors leveraging IP addresses and domains for phishing, malware distribution, and other cyberattacks. To counter these threats, leveraging public sources of information such as IP sets and blocklists is a powerful strategy. These resources are freely available online and can be integrated into Web Application Firewalls (WAF) like Fortinet, Imperva, and others to fortify your defenses.
Why Use Public Sources for Threat Intelligence?
Public sources of threat intelligence offer a cost-effective and community-driven way to identify malicious entities. These include:
- IP Sets: Collections of IP addresses flagged for malicious activity, such as spamming or DDoS attacks.
- Public Blocklists: Curated lists of IPs and domains associated with cyber threats, maintained by security researchers and organizations.
Advantages:
- Cost Efficiency: Free access to valuable data.
- Collaborative Defense: Benefit from community contributions and collective vigilance.
- Ease of Integration: Compatible with most modern security tools and WAFs.
Popular Public Sources for Malicious IPs and Domains
Here are some well-known resources:
1. Spamhaus
A leading provider of IP and domain blocklists, Spamhaus specializes in identifying spamming sources and related threats.
2. AbuseIPDB
This platform allows users to report and search for abusive IP addresses, providing a global perspective on malicious activities.
3. Emerging Threats Ruleset
Focused on real-time threat intelligence, this source provides blocklists and signatures for intrusion detection systems.
4. Open Threat Exchange (OTX)
A collaborative platform by AlienVault where users share threat indicators, including IPs and domains.
5. Project Honeypot
A community project that collects information on spammers and malicious bots, offering blocklists to protect networks.
Integrating Public Sources into WAFs
Web Application Firewalls (WAFs) like Fortinet and Imperva can be configured to use public blocklists for enhanced threat mitigation. Here’s how:
1. Fortinet WAF
- Import Blocklists: Use the FortiGate interface to upload custom IP or domain blocklists.
- Regular Updates: Automate the update process to ensure the latest threats are blocked.
- Traffic Analysis: Fortinet’s deep packet inspection can complement blocklists for robust protection.
2. Imperva WAF
- Custom Policies: Define rules based on public blocklists.
- Data Integration: Utilize Imperva’s API to pull threat intelligence directly into your policies.
- Anomaly Detection: Combine blocklists with Imperva’s behavior analytics for comprehensive defense.
3. Other WAFs
Many modern WAF solutions support importing blocklists in formats like CSV or JSON, making them versatile for integration with public sources.
Best Practices for Using Public Sources
- Validate Sources: Ensure the blocklists you use are maintained by reputable organizations.
- Automate Updates: Use scripts or APIs to fetch and update blocklists regularly.
- Combine with Internal Threat Intelligence: Augment public data with insights from your own environment.
- Monitor Performance: Track the impact of blocklists on network performance and false positives.
Enhancing Public Sources with isMalicious
While public sources are invaluable, combining them with advanced tools like isMalicious elevates your cybersecurity posture:
- Comprehensive Insights: Analyze IPs and domains with detailed historical data and risk scores.
- Customizable APIs: Seamlessly integrate public sources with tailored intelligence into your existing systems.
- Real-Time Alerts: Get notified of emerging threats faster than relying on static blocklists.
Stay Ahead of Cyber Threats
Leveraging public sources like IP sets and blocklists is a critical component of any robust cybersecurity strategy. When integrated into WAF solutions, these resources provide actionable intelligence to mitigate risks effectively.
Take the next step in securing your network. Explore isMalicious and discover how to combine public intelligence with cutting-edge tools for maximum protection.
Protect Your Infrastructure
Check any IP or domain against our threat intelligence database with 500M+ records.
Try the IP / Domain Checker